PowerShell Obfuscation Detection
Malware that uses PowerShell, the most prevalent use is the garden-variety stager: an executable or document macro that launches PowerShell […]
Malware that uses PowerShell, the most prevalent use is the garden-variety stager: an executable or document macro that launches PowerShell […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]
Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]
Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]
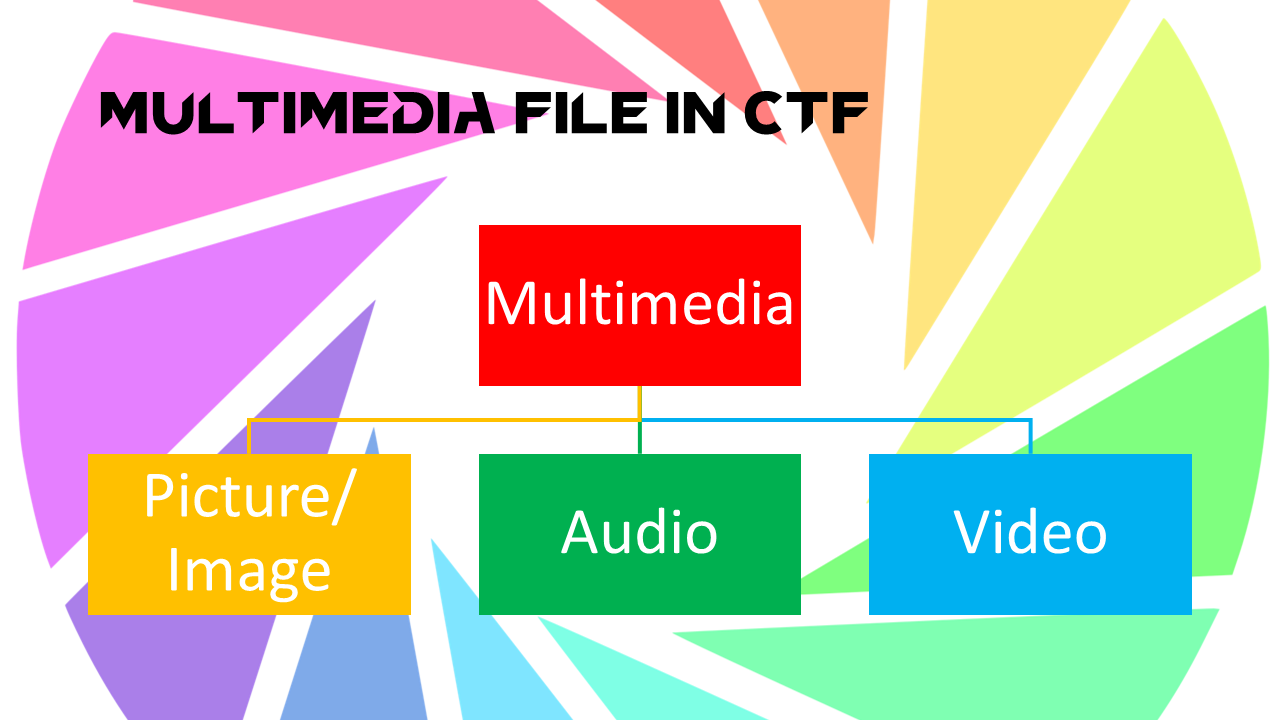
Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]