
Fields That Focused On | Capture The Flag Series | Reminthink Notes
Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]
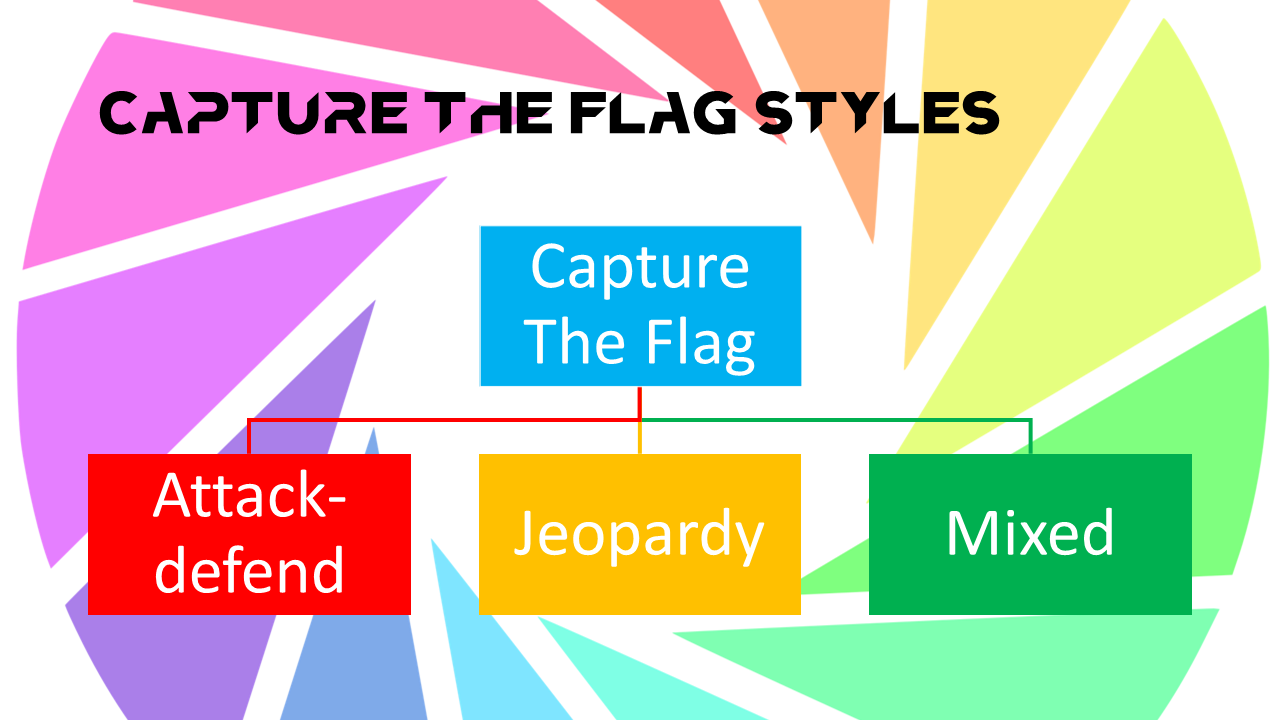
Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Capture the Flag (CTF) in computer security is an exercise in which “flags” are secretly hidden in purposefully-vulnerable programs or […]

Cannot Regenerate Same Password in Password Generator In common password generator, user can only can generate the random and one-time […]